Call for Master's Students 2020/21
Area 2: ONLINE CENSORSHIP AND ANONYMITY
Censorship and anonymity online. It's a very controversial topic. Partly because it's a double edge sword: it can help the good, but it can also help the bad. Just like with any gun: you can defend youself, or you can attack. We're with the good fellas.
The world is a dangerous place, and a mutted one too
I'm sure you've heard lots of stories on the news about online censorship. But honestly, in general one doesn't really pay much attention. I've always been insensitive to this problem. And the reason is that we live in a fantastic country (I know, I know, it has its nags). Until I was dragged by Diogo -- my PhD student -- and urged to look into this with more attention. Then it hit me. I was completely struck by realizing the extent to which certain states (big and small) implement censorship policies that cut people off -- their citizens -- and prevent free speech and free access to information. How many people are affected!
Have you thought about what'd be like to live without Google, Facebook, Twitter, Instagram, or Wikipedia? Or if you'd only be given access to state-controlled sites, knowing that the most relevant information would be twisted and manipulated to serve the state's own interests? Be prevented from accessing knowledge, asking difficult questions, searching for the truth, expressing your ideas, deciding what to do for a living? Be taunted, arrested, or killed if you resisted and refused to abide by the dictates of the government? It'd be bad!
As it turns out, more that 1 third of the world population is living in countries that enforce censorship policies. Just to give you an idea, check out the map below, taken from this recent article (which BTW it's a great read if you want to have an idea of what's going on out there -- this article was in turn a summary of a detailed report made by an organization named Freedom House in 2019).
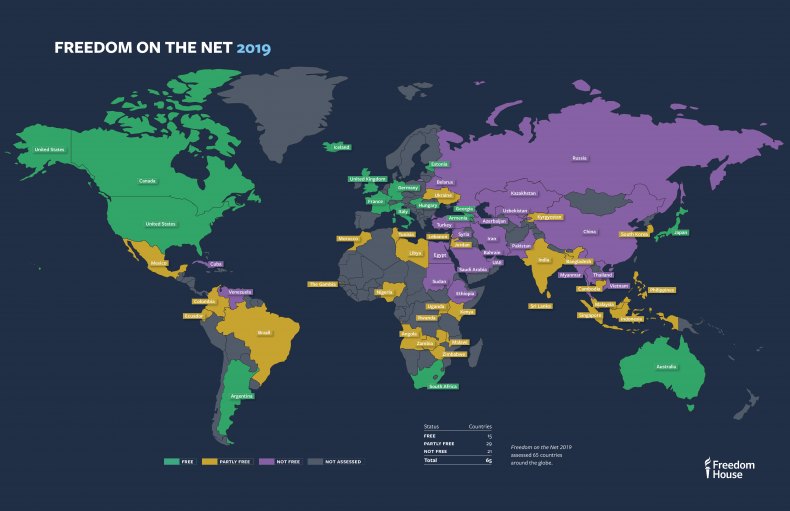
Do you see the world region colored in purple? Yep, in these countries, people are not free. Quoting from said study, the "vast majority of the 3.8 billion internet users worldwide live in countries where governments are using sophisticated technologies to turn social media into a tool for manipulation and social control." This is done by the governments of countries like China. How do they do this on such a scale?
The machinery of the Great Firewall of China
There is a vast arsenal of techniques that state-level censors implement in order to block people's access to the Internet's "free regions". Just as recently as in March this year, The IRTF wrote a wonderful survey about worldwide censorship techniques used to impair or block Internet traffic (the IRTF is one of the think tanks that's concerned about long-term research issues related to the Internet). There, you see a magnificent list of methods implemented at all layers of the network stack.
Guess which state implements these techniques more broadly and strictly? The People's Republic of China. IP address blocking, protocol profiling and filtering (e.g., Tor, and OpenVPN), deep packet inspection, DNS spoofing/DNS cache poisoning, URL and keyword filtering, malicious insertion of TCP resets, deanonymization of Twitter users through password resets, VPN blocking... (Note: VPNs are centralized and represent a big risk against being forced to show accessed content to the government.) All of this is implemented by the Big Brother using an incredible apparatus commonly known as The Great Firewall of China. Here's some great articles in The Guardian and Bloomberg about the GFC. Wouldn't it be great if we could circumvent it?
Let's open a crack in the wall
Actually... WE DID IT! For over a year, we've been building a tool named Protozoa, which provides the ability to circumvent the censorship techniques mentioned above and allow its users to freely access the Internet. Last month, we finished our system, and rented a few servers in several countries that implement blocking policies. By testing Protozoa on those servers, we were actually able to access blocked websites. In which countries? India, Russia, and yes, China :) Isn't it cool?
How does it work? Have a look at the picture below. Imagine Alice lives in a censored region. She has a brother, Bob, doing his PhD in the US. They are very friends and have regular chats on Whereby, the web streaming service that lets you make video calls. If Alice tries to access Youtube directly, she gets blocked. A workaround to this problem is to ask Bob to install Protozoa, and set it up to act as a proxy to Alice's IP traffic. Alice launches Protozoa locally, so that both endpoints would create a tunnel, and the traffic relative to Alice's visit to Youtube would be transparently routed through Bob's computer. This concept is very similar to installing a VPN server or an SSH proxy on Bob's endpoint, but with one important difference: Protozoa's payload traffic is exchanged through a covert channel mounted over Whereby's point-to-point video stream.

Concretely, what Protozoa does is to transparently replace the data associated with the video camera's frames generated by Alice' and Bob's cameras with payload IP packet data. This will effectively destroy the image signal exchanged between both users, preventing them from seeing each other; but the audio is left unchanged, which means they can still hear each other and keep the conversation going while Alice accesses YouTube in the background. We do this in a way that the properties of the resulting network packets exchanged between both endpoints will look exactly the same as any unmodified Whereby video calls in the eyes of a censor. In this way, a censor that can observe all the communications within the censored region won't be able to tell that an embedded IP packet stream is being piggybacked by the Whereby application and therefore cannot prevent this covert communication unless it would block Whereby traffic entirely.
At this point you might be wondering: "What prevents the censor from blocking Whereby anyway?" The answer is: it can, but it won't make much difference. The reason is that Protozoa is not strictly dependent on Whereby, but it works with any web streaming application based on WebRTC. WebRTC is a W3C standard that defines protocols and APIs for real-time media streaming web applications. It is supported by all major browsers and it is widely used in popular web streaming applications, including Hangouts, Discord, Houseparty, Gotomeeting, or Jitsi, and for gaming and video broadcasting. Just check out this extensive list of WebRTC apps out there. To defeat Protozoa, a censor would not only need to cut off Whereby or a couple of these services; it would need to block all WebRTC traffic which would cause unbearable collateral damage to the economy (how dependent are we today on media streaming services!). Isn't it cool?
The next big step: A censorship-resistant overlay network
With Protozoa, we can open a crack in the wall, but now we want to expand this crack. If you think it carefully, in order to circumvent censorship mechanisms, our system requires having someone that the user trusts in the free Internet region to run a proxy service on the user's behalf. This is perfectly feasible for many individuals that have close friends or acquaintances abroad, living in free countries. However, many people in censored countries may not have such connections and therefore will remain deprived from free access to information.
To overcome this restriction, our next step is to build a Censorship-Resistant Overlay Network (CRON). CRON is a distributed system that will consist of a large network of nodes interlinked by WebRTC video streaming applications. These nodes will be able to communicate covertly using Protozoa-enabled tunnels. Some nodes are located within the censored region (clients) and others in the free region (proxies). Acting globally and in a coordinated fashion, the nodes will assist each other in providing access to the proxies in the network, especially assist such clients that do not have an immediate connection to some proxy.

The figure above helps to illustrate what we envision. It shows three groups of nodes -- G1, G2, and G3 -- where each node NX represents the computer of an individual user (X) of the CRON network. Some nodes have connections in different groups, for example N1 can participate in G1 and G2. Some users are located in the free region (e.g., N2) and therefore can act as Protozoa proxies. Some other users do not have any direct connection to proxies, for example, N3, and are therefore precluded from establishing direct Protozoa channels with the free world. Essentially, we want to overcome this limitation by reaching out to the proxies through a path of intermediate client nodes linking cut-off clients to proxies, e.g., through N1.
Open challenges and system design
To build such a system, we need to overcome several challenges at three main levels:
- C1: Routing: This involves addressing the problem of how cut-off clients can find a path through the CRON network until reaching a proxy. Remember that Protozoa can only transmit covert data between nodes connected in the same video call, in a point-to-point fashion. We need to be able to create multiple video calls for each group, enable multicast / broadcast communication within each group (both for allowing the transmission of control messages between nodes and payload data transfers), discover which groups are active at a given point in time and which proxies are available, and find a path through the CRON network.
- C2: Security and trust:This aspect is also crucial. From the security point of view, we need to ensure, e.g., that the channel that results from the composition of multiple individual Protozoa tunnels remains secure, guarantee that the proxies are indeed located outside the censored region (in particular we may need to obtain location proofs), and that malicious clients are not leveraging proxies for accessing illegal content. There's also a number of interesting trust-related issues. In particular, it will be necessary to implement mechanisms that give clients the confidence that the proxies are trustworthy, that they are not controlled by an adversary.
- C3: Forensic resistance: Studies indicate that many users avoid using censorship-resistance tools because they leave traces on their computers (e.g., the executable binary of the tool, logs) that could be detected by physical inspection of the device. This is actually performed in many coutries by state delegates with the purpose of forcing their subjects to disclose any activities that they might have enacted against the state. It is therefore important that CRON software can resist forensic inspection by leaving as less traces on the nodes as possible.
We plan to address these problems by designing CRON as a layered software architecture as shown below.

Essentially CRON will consist of a middleware layer that runs on top of the WebRTC protocol layer and provides application-level communication services between clients and proxies. Internally, the CRON middleware is structured into several components. The transport layer provides point-to-point communication between two nodes using covert tunnels: this functionality will be provided by Protozoa. The circuit layer will sit on top of the transport layer and will address all the issues discussed in C1 and provide a communication API for the upper layer. The security monitor and the anti-forensic shell consist of cross-cutting components that will act upon all layers of the communication and address the challenges C3 and C3, respectively.
Master's thesis topics
Which brings us to our last subject of this document. There are three thesis topics that naturally emerge from the system design we envision for CRON:
- CA1:This thesis will be focused on the design of the circuit layer.
- CA2:This topic focuses on the design of the security monitor.
- CA3:This proposal will be about the anti-forensics shell.
Since they share the common goal of contributing to the design of the CRON system, these theses will be realized in close collaboration with each other, and will be assisted by both me and my PhD student Diogo Barradas. We describe each topic in more detail in the main page. If your are interested, go have a look.